What began as a typical online transaction swiftly transformed into an enigmatic journey through the digital realm when a Reddit user discovered nearly 800GB of unexpected data on a supposedly new 1TB SSD Rather than sitting vacant and available for installation, the drive was filled with top-tier, professional-quality applications.
A Journey Laden with Tens of Thousounds Worth of Musical Equipment
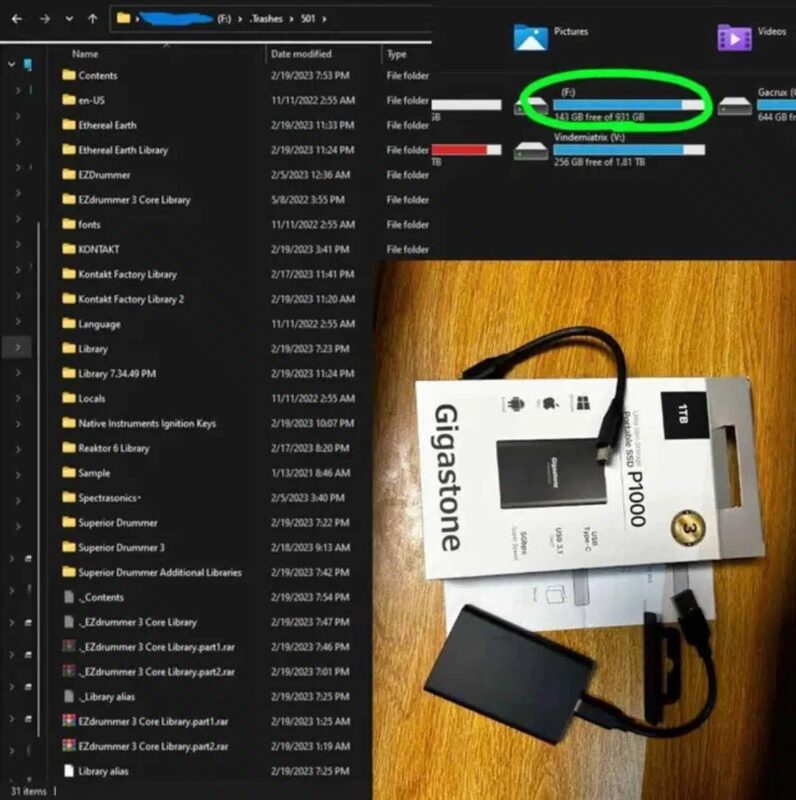
The Reddit user nicknamed All-Seeing_Hands , had recently purchased something he thought was brand-new solid-state drive Similar to numerous tech-savvy individuals, he chose to examine the contents of the SSD prior to formatting it.
To his astonishment, the drive wasn’t vacant—it was teeming with high-end music production equipment, including Kontakt and Reaktor , two extensively utilized industry-standard programs by expert composers and audio engineers Collectively, the software installed on the SSD could amount to a value of several thousand dollars.
Once the user shared details of the event on Reddit, they quickly gained widespread notice. Other individuals verified that the documents involved were authentic and held considerable business worth. A simple procedure for setting up equipment unexpectedly turned into a major point of discussion on the internet, leading to numerous theories and arguments.
Theories and Suspicions Surround the Origins of the Drive
The existence of this costly software on what was claimed to be a new SSD soon gave rise to various speculations. Some Reddit users theorized that the device could potentially have a returned item Resold without adequate data erasure.
In retail environments, particularly with electronic items, returned products frequently return to the shelves following only basic checks. This practice might account for why highly confidential data could end up in unexpected possession, assuming the initial user did not clear the device's storage and the outlet neglected to confirm its condition.
Other expressed more reserved hypotheses. Some thought the documents could have been intentionally planted As part of a scam or malware campaign, this might involve tricking purchasers into installing contaminated software masked as useful applications. Regardless of the method used, this scenario highlighted vulnerabilities in the authentication and resale processes for electronic devices.
Safety and Regulatory Issues with Uncorroborated Information
Apart from the intrigue and enthusiasm surrounding the discovery, cybersecurity professionals caution that events of this nature underscore significant dangers. Installing pirated or altered software unintentionally can lead to violations of licensing contracts. Furthermore, these files may act as conduits for malware. malicious software, surveillance programs, or concealed entry points , compromising the user's data and privacy.
Organizations like the Electronic Frontier Foundation (EFF) have consistently promoted prudence regarding digital material of uncertain source. Specialists stress that each new or dubious gadget should be scanned and securely wiped Before using it. Despite appearing genuine, a file might have been subtly altered in such a way that the issues only become apparent once the software becomes operational.
An Alarm Bell for Both Retailers and Customers Alike
The event has likewise sparked renewed worries regarding Quality assurance in consumer electronic sales Customers assume that new items are unused, and breaching this expectation might indicate deficiencies in internal procedures. Both retailers and producers could benefit from reviewing their policies concerning product returns and remanufacturing, making sure that devices such as hard drives are genuinely pristine prior to being resold.
For buyers, this event is a reminder to stay cautious, even when unpacking brand-new gear. Taking the time to inspect, scan, and wipe a device isn’t just good practice—it could prevent serious security issues down the line. In this case, a simple check turned into a headline-grabbing revelation and a stark lesson about the hidden layers of modern tech.
Enjoyed this article? Sign up for our complimentary Newsletter for captivating tales, special material, and up-to-date information
To find similar stories, check out Indiandefencereview.com